I have to admit it – I do love Linux
Hopefully I’m not the only one that can combine Windows, Linux and OS in a daily life and love all platforms – but in real life it’s not that common that Windows administrator like Linux and Linux administrator sure hates Windows.
I have never been a huge fan of ISA/TMG/UAG mostly as I believe they are overcomplicated to manage in SME environments and perform badly on general hardware. Running NIX* based firewalls are much easier (iptables for example) and appliances out there (PFSense) are really easy to use and gives a great overview of threats. Of course iptables does not offer a reverse proxy as you can do in TMG/UAG but when Microsoft decided to pull the plug on TMG I decided that I should evaluate a few Linux options.
A popular choice would be Apache as it’s really a mainstream product handling http(s) traffic for millions of sites. Apache is easy to configure if you’re used to apache directives and vhosts. After a few hours reading I realized that Apache wouldn’t work as there is no support for NTLM and that Microsoft RCP traffic (Famously used in Outlook Anywhere) is not supported (Apparently Microsoft tweaks the http protocol in a way that ûber geeks don’t like).
My next option where Squid, the well-known cache socks proxy that has been around for ages and its capability list grows for every day. After some reading it seemed that Squid would do the job. However as normal when it comes to Linux systems it takes a while until new releases reaches mainstream distributions like Fedora, CentOS and Ubuntu. If you want NTLM pass-through you should go with at least 3.2 release as it’s the latest version. I had various results with earlier releases and even had a few problems compiling all the libs for 3.2 on earlier dists. So make things easier if you want to try out download Fedora 18, yes the build that some Linux geeks describes as the worst Fedora build ever J
Fedora 18 has Squid 3.2 already included in the source path and is easy install. The latest builds also do not require any special tweaking to get RCP traffic flowing as earlier releases did. 3.2 is also the first release that has HTTP1.1 built in as well as IPv6.
After spending hours on configuring a match on target servers in terms of authorization and configuring various autodiscover services to match the changes things started rocking! I successfully managed to get all Exchange services (Autodiscover, Outlook Anywhere, EWS and OWA) working externally in my home lab. Next “victim” where my lovely Lync 2013 installation where it was time to publish my meet/lync servicepoints for meetings and more important the Lync 2010 mobile client. I didn’t have a single issue there mostly as Lync offers a separate application for external access. After these services where running I published the Office Web App service and a Sharepoint site (The one you are reading now).
Lync where about to change that.
If everything worked fine why would you steer away from squid one might ask? Well it’s all thanks to Lync 2013 mobile clients that just were released. Lync 2013 for mobile clients introduced a new authorization mechanism called Webticket (A form of OAuth) and whatever I tried that did not work with squid. So searching again for options I came across the ARR module in IIS that Microsoft itself claims to be the only supported reverse proxy for Lync 2013 (Yea not even TMG is supported even if it seems to work but as the product is gone I guess it would not make sense to officially point at it.)
ARR to the rescue
So I decided that I really wanted to try out the new Lync client and give VoIP a try (as you can read about here) and therefore rolled out a Windows 2008 R2 image from VMware and installed ARR. That failed. Installation went well but every time I tried to hit a resource behind the proxy the work process crashed. Then I tried the new beta version of ARR and that crashed as well. Being short on time and happened to have a 2012 image so I tried that one and here things started to flow nicely. Happy with the results I moved all my Lync servers to the new ARR installation and started my fat Lync client that runs externally on the edge server. That worked without any issues. Now, happy with the results I fired up my Lync 2013 mobile client on my lovely Nokia 920 WP8 device and I were able to login. Great success!!!!
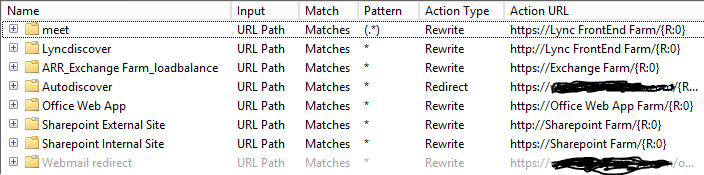
As adding rules where even easier than in Squid or Apache I decided to move all my servers to the ARR server farm requiring me to have endpoints for Lync, Exchange, SharePoint and Office Web Apps. After about 20 minutes I had migrated all the servers and re-used the external IP address from my Squid installation on the IIS ARR service. I did not experience any issues with Exchange, SharePoint or Office Web Apps after the migration, everything worked as it did before on Squid.
The only “drawback” I can find would be around resources as Windows takes a lot more resources than I Linux box I can run on 512Mb of ram without any issues. Trying to do that on a Windows Server 2012 box is another story.
Apart from that I believe that IIS ARR will be a suitable and stable replacement for any other solution out there. Another upside would be that you can cluster (NLB) the ARR servers for HA.