We all know networking can be hard if you have never had any deeper experience than learning that you need to have the correct subnet mask and gateway so your server can communicate on the network.
I can honestly admit that I’m not a network guy by heart but I have also realized that you need to understand some core components in networking to be able to tell the network guys that the problem is on their side 🙂 So, as always doing labs will help you understand that. Most networking guys does that in simulators, there are plenty of them available, both from networking manufacturers like Cisco and from third party like GNS3. I’ve done all that but real life labs for me has helped to understand the basics, and more importantly understood the consequences when things go wrong 🙂
Its way better to put your lab into use when you do networking, if you do thing wrong you might end up in loosing Internet connectivity or your email flow stops working. So what equipment do I have at my disposal? First I’d like to say that i do prefer working with Juniper, not that the hardware is in anyway better for my purpose, but the CLI gives you a lot more options, in particular when your doing LABs. JuneOS configs are not instantly activated. That means, that I can do the commands I’m planning to configure and review them before I commit them. I can also place an “automatic undo” on an command that I’m thinking might blow up in my face and that will make me loose some of the network connectivity. Junos would automatically rollback to the previous configuration after a number of minutes (default is 10) so you would never be looked out of your own network, really useful in both labs and production networks.
 Core network
Core network
Yes, writing a title like “Core” in a home lab does not make sense at all, but it gives you the feeling that you are simulating an real production environment, for example an office or a datacenter. Obviously you will not be able to simulate the hardware in a datacenter at home (You could of course do that in GNS3 but that requires a lot of CPU resources also) but as I said before I would like to do my labs as real as one could (When you read my other blog posts you will see that everything that I’m doing in the lab is actually working as in production and in some cases are production quality). For the Core Switch (sits in my closet) I’ve picked a Juniper EX 3300 switch on EBay for $800, a bargain if you consider the fact that is has four 10 Gigabit Ethernet ports (SFP), 24 PoE Gigabit copper ports and comes with Virtual Chassis as default (Junipers switch-stacking feature that removes the need to do Spanning Tree between switches). It can also (with the right license) do OSPF and OSPFv3 (IPv6 OSPF), BGPv4, RIP and other routing protocols, has support for most Multicast protocols, both L2 and L3 (Important for me as I work in a Multicast environments all day). Of course it does L3 easily, including “routed VLANs” and support routing instances to separate traffic in the form of an Virtual-Router.
 Firewalling is, and has always in my home been done in software. There are, potentially benefints of running a hardware based firewall, i.e. if you need to troubleshoot a firewall issue and your firewall is broken would potentially leave you without internet access…. shit… The benefints, however does not match the limitations. First, throughput, very few firewalls do 1 Gbit/s+ (consumer or SME) of bandwidth. For me with 500 Mbit/s Internet that leaves very few packets left to do internal firewalling, for example between LAN and DMZ. 15 years or so I’ve started with m0nowall running on a dedicated
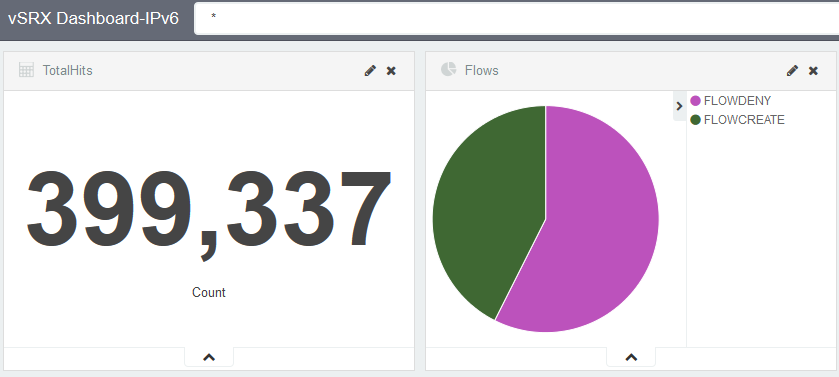
Firewalling is, and has always in my home been done in software. There are, potentially benefints of running a hardware based firewall, i.e. if you need to troubleshoot a firewall issue and your firewall is broken would potentially leave you without internet access…. shit… The benefints, however does not match the limitations. First, throughput, very few firewalls do 1 Gbit/s+ (consumer or SME) of bandwidth. For me with 500 Mbit/s Internet that leaves very few packets left to do internal firewalling, for example between LAN and DMZ. 15 years or so I’ve started with m0nowall running on a dedicated server desktop pc. 15 years ago you could more or less not buy a firewall capable of doing stateful inspection at gigabit speeds. However m0n0fwall was replaced with PFSense and now is finally replaced with a clustered (soon-to-be-clustered) vSRX (Virtual Juniper SRX firewall) running on ESX hosts. I must admit that I didn’t expect that the virtual Juniper would work that great, of course all firewalls out there today are software based (wrapped inside hardware) but it has worked really well. As seen in the screenshot to the left firewall sessions are reported into an ELK stack (have an older blog here based on PFSense) and gives me great troubleshooting tools over time (i.e. on Sunday my webmail stopped working, what happened in the firewall at that time?)
Access Network
My access network is not that great, as you might expect, I have only one access switch in my living room and another one in closet #2 where my backup NAS sist. They are based on the Cisco SG300 series and offers L2 and L3 (Intra-VLAN routing). Currently is does only L2 as all L3 is done in the EX3300. On top of that I also have an Cisco AP that is responsible for the Wi-Fi in the house, the Access Point (as the name suddgest) only bridge traffic from the Wireless WLAN SSIDs to L2 VLANs i.e. does not do any routing on the wireless network. I have three SSIDs in the house, one general Wi-Fi network where I place my laptops, phones etc. that does only require limited internal network access, the next SSID does 802.1x for laptops that do require internal access (Have 802.1x enabled on the wired network as well). The third network is an Guest network that I rarely use as we have excellent mobile coverage and most data plans in Sweden are so cheap so few guests actually ask to get access.
Routing
For the most part of my lab home things in the network area are somewhat “different” compared to a standard home. The whole network routing is based on OSPF, from the core towards the firewall. The core switch includes routing instances meaning some traffic will not be routed on the switch to reach its destination but instead has to pass the firewall. Routes are exchanged between the Juniper EX3300 and the (virtual) Juniper vSRX. There is also an virtual vMX router that is not really in use but used for lab purposes.
IPv6
The network runs IPv6 in some parts, I have not migrated to IPv6 fully yet but the Office Network, DMZ and Server network runs IPv6 including OSPF routing (v3). IPv6 connectivity is, I’m afraid not yet supported by my ISP (ComHem) even they said that it will come a few years back. So thanks to the excellent services of tunnelbroker.net (HE) I can enjoy IPv6 connectivity without any compromised speed, reaching 500 Mbit/s without problems. My HE runnel is terminated in my vSRX firewall as a regular IP tunnel and I inject an default route into OSPF so the traffic can flow both ways.
Currently my /48 that HE was so kind to give me is not allocated as I started with the default /64. So the 64 has currently been sliced into four /66 networks that I have allocated for my routing-instances/security zones. I’m running link networks (OSPF links) in the private IPv6 space (LinkLocal) at the moment, as I have not really decided if I should move to my dedicated /48 and start from scratch now when things are working.
This is one of the things that makes IPv6 absurd – the number of IP-addresses that’s available. My /48 contains more IP addresses than the entire IPv4 block, and they are all mine… But as I do routing on a switch level (my EX3300) I want to avoid generating smaller segments than the /66 I have split up my /64 into now.
IPv6 works somewhat ok, but some sites has not properly configured IPv6 – They have AAAA records configures that points to an IPv6 adress that is not properly configured so when my Windows Dual-stack OS founds an IPv6 address it obviously tries to use it and .. fails. Some sites I use from time to time seems improperly configured, like VMWare, QNAP etc. The only workaround is to either use another computer (without IPv6) while accessing them or disable IPv6 temporary.
Another problem I got into was the fact that HE blocks some ports, sure we expect port 25 to be blocked outbound to try to stop spam, but HE also blocks inbound SMTP connections leaving my shiny email gateway disconnected completely from the IPv6 world. The same was noticed for IRC traffic now flowing either on the HE tunnel. First I was sure this was a firewall issue but after troubleshooting I’ve noticed that the packets didn’t even hit the FW. Contacted HE and they replied within only a few hours notifying me about the block. The only way to eventually get this sorted out was to pass all their IPv6 exams (Sage level) and apply for an exception to be made. Once that was done I was able to receive IPv6 emails.
IPv6 Applications
Even if this is not directly related to networking in general I’d like to share my experience with IPv6.
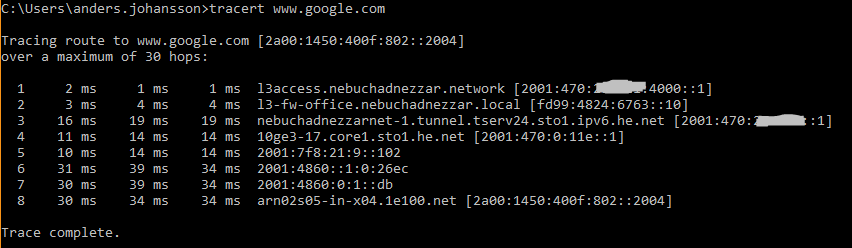
I have included a few traceroutes to show how traffic is flowing. I’ve masked my public IPv6 network, not really thinks that has any effect but just a good practice. As you can see I have no PTR records (this has now been done) for my IPv6 network yet. I have configured an external DNS server within the HE portal but for some reason its not working properly. Now it’s working fine and I have managed to grab myself a new domain just for PTR lookups, sweet. I’m running a DNS server on both IPv4 and IPv6.
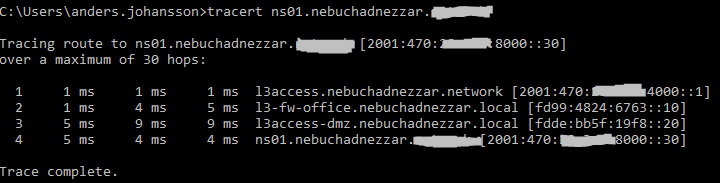
Separated Routing instance
Traffic flowing between my office network and DMZ, passing the firewall as its using its own routing-instance on the EX3300
IPv6 Internet Access
Traffic from my IPv6 Internal Network (4000 = Office) to Google, all over IPv6 and HE tunnel:
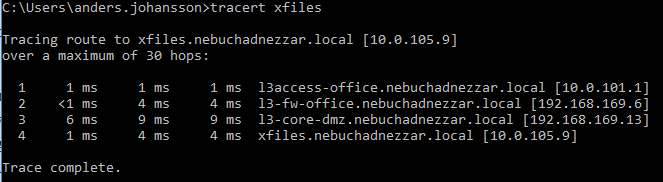
IPv6 Internal Routing
Traffic from my IPv6 Internal Network (4000 = Office) to another host, also sits in the DMZ and therefore has to pass the Firewall.